Exploits, Reverse Engineering & more!
Best in the industry
Hardware, Software, IoT, everything in between.
We have your back
Malware Analysis & Development
Find out how it works
With over 20 years of experience in low-level systems analysis and offensive security, we specialize in uncovering the inner workings of complex software systems, identifying vulnerabilities, and crafting innovative solutions that push the boundaries of cybersecurity.
Here at GironSec, we're all about hacking, reverse engineering and exploit development. Anything low-level is our game.
We evaluate the security of embedded systems, chipsets, and hardware interfaces (e.g., JTAG, UART, SPI) to uncover physical attack vectors and firmware-level vulnerabilities. Our hardware assessments address threats such as side-channel attacks, tampering, insecure boot processes, and supply chain risks—helping protect high-value and mission-critical systems.
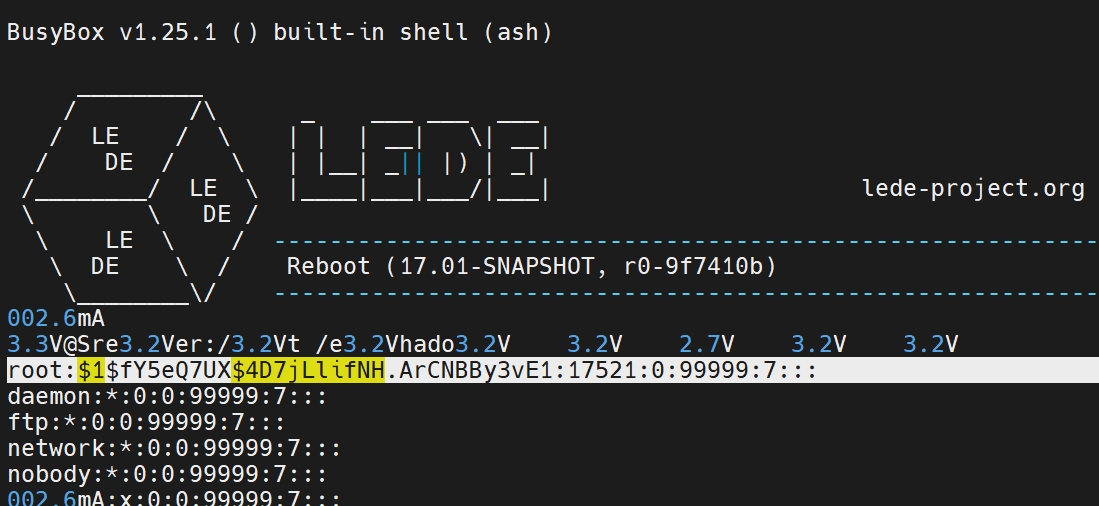
We perform low-level software analysis to deconstruct binaries, firmware, and proprietary systems. This service enables clients to uncover undocumented features, analyze legacy software, validate third-party components, and identify vulnerabilities within closed-source environments. Our work supports secure integration, compliance validation, and IP protection.
We assess iOS and Android applications for vulnerabilities that could compromise user data, system integrity, or backend services. This includes analyzing insecure storage, flawed authentication mechanisms, improper permissions, and third-party library risks. Our testing ensures mobile apps meet modern security standards and regulatory requirements.
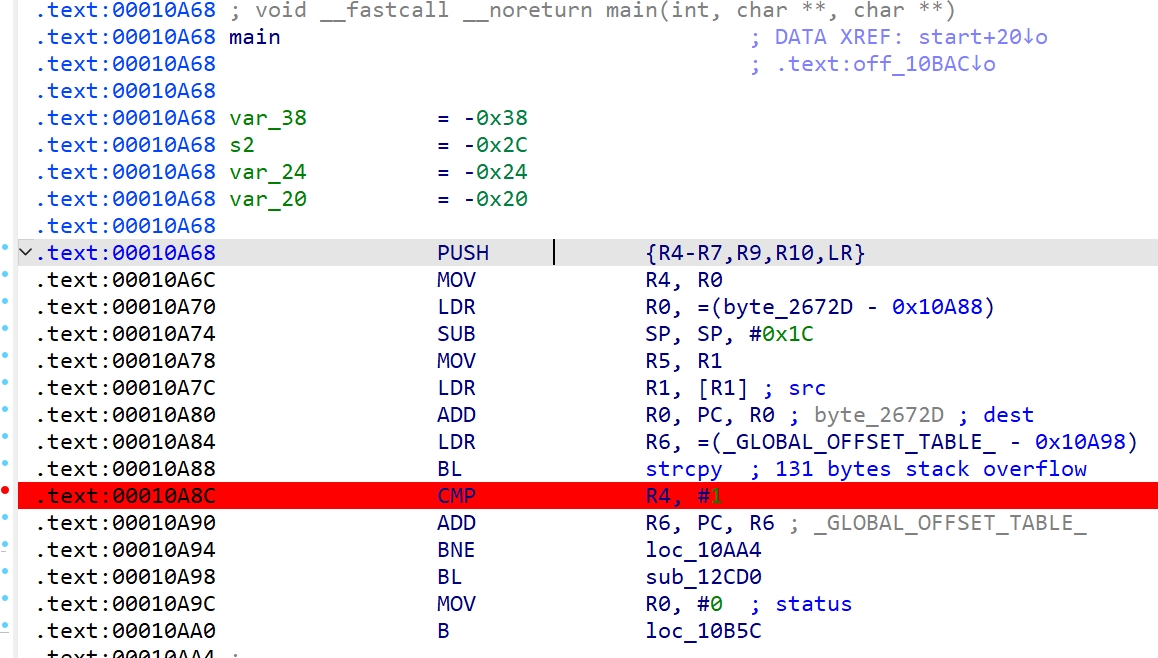
We discover and validate exploitable vulnerabilities through the creation of custom proof-of-concept exploits. This includes memory corruption (e.g., buffer overflows, ROP chains), logical flaws, and privilege escalation techniques. Our insights help organizations understand the severity of risks and guide effective mitigation strategies.
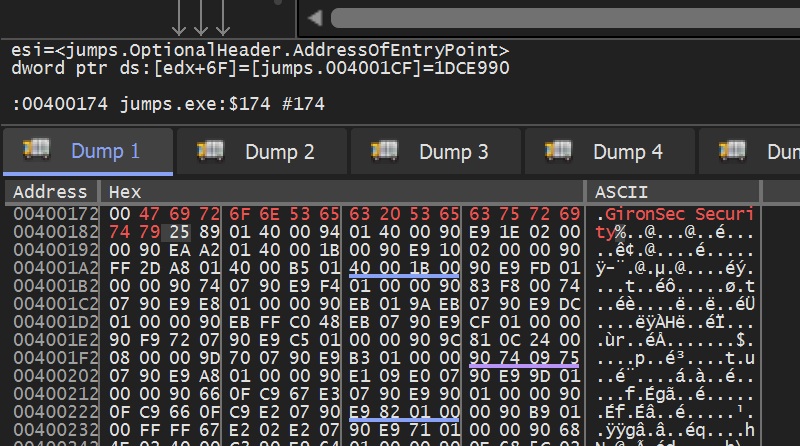
We dissect malicious code to understand behavior, identify indicators of compromise (IOCs), and support incident response. Our malware analysis services provide detailed intelligence on threat capabilities, persistence mechanisms, and evasion techniques—essential for improving detection and defending against advanced threats.
Our team are experts at finding and exploiting applications and websites alike on all platforms from single hosted to cloud based. Thin clients, thick, and everything between, we know our stuff.
Our team of experts has done it all. From BGA chips to unpacking ransomware, if you need something reverse engineered or exploited, we'll take a crack at it.

We are a specialized offensive security team focused on deep technical analysis, vulnerability discovery, and real-world adversarial simulation. Our mission is to help organizations understand and mitigate complex security risks across software, hardware, and mobile platforms.
Our expertise spans advanced reverse engineering, where we deconstruct binaries and firmware to expose undocumented functionality, supply chain risks, and embedded vulnerabilities. We develop custom proof-of-concept exploits to validate critical flaws in applications, kernels, and system components—enabling informed remediation and improving organizational resilience.
Through comprehensive penetration testing, we simulate sophisticated threat actor techniques to assess the security of networks, cloud environments, and web applications. Our red team operations go beyond checklists, delivering strategic insight grounded in technical depth and attacker realism.
We analyze malware at both static and dynamic levels to support incident response, threat intelligence, and detection engineering. Our team uncovers behavioral signatures, command-and-control mechanisms, and obfuscation strategies used by modern malware families.
On the mobile front, we evaluate iOS and Android apps for client-side flaws, insecure APIs, data leakage, and insufficient protections against tampering and reverse engineering—guided by the OWASP Mobile Security Testing Guide and platform-specific best practices.
In the hardware domain, we assess embedded systems for physical attack vectors, insecure firmware, and weak interface protections. Our work spans everything from bootloader validation and firmware extraction to side-channel and fault injection testing.
Driven by precision, discretion, and deep technical capability, we deliver high-impact results that help organizations stay ahead of evolving threats.
Fill out the form below and we'll get back to you as soon as possible.